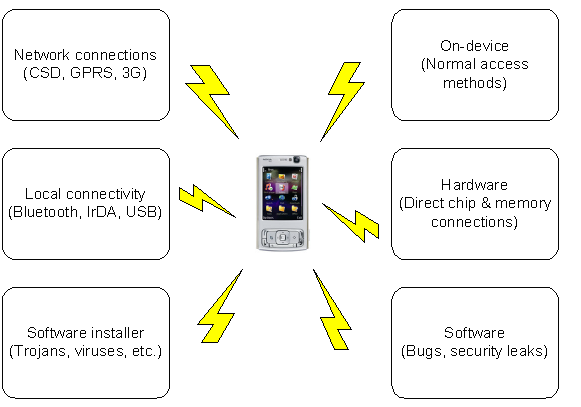
Device security
The superior mobility and connectivity of mobile devices constitutes their greatest threat, and allows intruders to try different attack methods against the device. The figure below illustrates the most common methods of attack against mobile devices.
Due to the nature of mobile devices, including the potential vulnerabilities mentioned above, you should consider the following points when designing your application:
If a mobile device is lost or stolen, confidential information (for example, calendar and contacts) can be read even by those with little expertise.
Users can access confidential information and files at any time, including reverse engineering of software and algorithms.
Data can be transferred from and to the mobile device through different methods, even accidentally.
Users may detach removable media or the battery at any time, which can cause data loss or corruption.
When you handle confidential information in your application, remember that with sufficient motivation and resources there are always ways to extract information from a mobile device. As the level of software security improves and attacks become less practical, interest in hardware attacks may in turn increase.
In the continuously evolving digital world, every application should have a certain level of robustness against a changing and hostile environment. Applications should be prepared for data corruption and alteration, network and storage blackouts, plug-ins and components that misbehave, malicious attackers, and, perhaps most importantly, user errors.
The Symbian platform security architecture is designed to protect mobile devices and their contents.
For more details, see Device security mechanisms.
Copyright ©2010 Nokia Corporation and/or its subsidiary(-ies).
All rights
reserved. Unless otherwise stated, these materials are provided under the terms of the Eclipse Public License
v1.0.