Certificate and Key Management Overview
The Certificate and Key Management component provides authentication services for Public Key Cryptography .
Purpose
The main purpose of the Certificate and Key Management component is to provide validation services according to the Public Key Infrastructure (PKI) for X.509 Certificates.
The Certificate and Key Management component provides interfaces for the following:
-
Storage and retrieval of certificates
-
Assignment of trust status to a certificate on an application-by-application basis
-
Certificate chain construction and validation
-
Verification of trust of a certificate
-
Generation of asymmetric key pairs
-
Protected storage of keys
-
Key import and export
-
Authenticated execution of private key operations
Required background
To understand Certificate and Key Management in detail, you need to have a basic understanding of the following:
Key concepts and terms
- Certificate
-
A certificate is an electronic document that binds an identity to a particular public or private key pair. It is commonly used to authenticate cryptographic public keys.
Certificates are issued by a Certification Authority (CA). They usually include information such as a label, serial number, validity period, certificate format (for example, X.509) and algorithm type (for example, MD2RSA).
- Key
-
A cryptography key is a constant value applied using a cryptographic algorithm to encrypt text or to decrypt encrypted text.
Keys are classified as symmetric and asymmetric based on the type of algorithm applied. If the same key is used for both encryption and decryption, it is symmetric. If different keys are used for encryption and decryption, they are asymmetric. Asymmetric keys exist in the form of a public and private key pair, where the public key is used for encryption and the private key is used for decryption.
- Certificate Store
-
A certificate store is a database or a file that stores and manipulates certificates.
The certificate store provides the following functionality:
- Key Store
-
A key store is a repository of keys that can be retrieved and used to accomplish a variety of tasks.
The key store provides the following functionality:
- Token
-
A token is a physical instantiation of an object, such as a certificate or a key, stored in a phone. Each token belongs to a group of tokens called a token type. For example, an X.509 certificate is a token which belongs to the X.509 token type.
Architecture
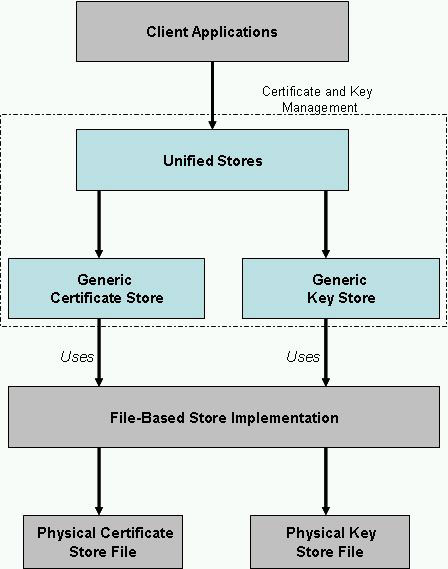
The following diagram shows the basic architecture of the Certificate and Key Management component. The blocks in blue are internal to the component.
The various blocks in the basic architecture diagram of the Certificate and Key Management component are explained as follows:
-
Client Application : This is a typical application that accesses the certificates or the keys of the device through Certificate and Key Management component.
For example, a web browser that wishes to load a bank's web page to perform a money-transfer operation (in a secured mode using an https connection) first checks the device's certificate store for a certificate that trusts the bank's server and then loads the particular page.
-
Unified Stores : The Unified Stores APIs form the primary access point for client applications to use certificates or keys stored in the device. The Unified Certificate Store provides a unified view of all the certificates in the device while the Unified Key Store provides a similar view of all the keys in the device.
-
Generic Certificate and Key Stores : These are the various certificate and key stores in the device.
-
File-Based Store Implementation : The certificate and key stores use Symbian's file-based store implementation . Based on the operations to be performed on the keys and certificates, the file-based implementation updates the physical certificate and key store files.
APIs
The following table lists the key APIs of the Certificate and Key Management component. The table lists APIs that perform the following tasks:
-
Provide implementation for certificate and key stores, and for manipulating various types of certificates.
-
Perform different types of ASN.1 (Abstract Syntax Notation One) encoding.
| API | Description |
|---|---|
|
Unified Store APIs |
|
|
Provides a common implementation for all certificate stores in the device. |
|
|
Provides a common implementation for all key stores in the device. |
|
|
Certificate APIs |
|
|
Provides implementation for parsing and matching the X.500 distinguished names. |
|
|
Provides implementation for parsing and matching attribute types and values, as defined by the X.520 standard. |
|
|
Provides implementation for manipulation of X.509 certificates. |
|
|
Provides implementation for X.509 certificate chain validation. |
|
|
Provides APIs for encoding and decoding of RSA public keys. |
|
|
Provides APIs for manipulating various X.509 certificate extensions. |
|
|
Provides implementation for construction and manipulation of WTLS (Wireless Transport Layer Security) certificates. |
|
|
Provides implementation for manipulation of WTLS names. |
|
|
Provides implementation for manipulation of RSA public keys associated with WTLS certificates. |
|
|
Provides implementation for validation of WTLS certificate chains. |
|
|
ASN.1 Encoding APIs |
|
|
Encodes Big Integer objects. |
|
|
Encodes bit strings (for example, keys). |
|
|
Encodes Boolean values. |
|
|
Encapsulates already encoded information. |
|
|
Wraps other encoding objects and provides them with an explicit tag. |
|
|
Encodes time-related objects. |
|
|
Encodes TInt objects. |
|
|
Encodes NULL values. |
|
|
Encodes object identifiers. |
|
|
Encodes octet strings. |
|
|
All ASN.1 primitive type encoding classes derive from this class. |
|
|
Encodes printable strings. |
|
|
Encodes the SEQUENCE and SEQUENCE-OF data types. |
|
Typical uses
The Certificate and Key Management component performs the following tasks:
-
Validating certificates in PKIX
-
Adding certificates
-
Finding certificates
-
Managing applicability and trust settings
-
Removing certificates
-
Retrieving certificates
-
Creating keys
-
Importing keys
-
Exporting keys
-
Retrieving keys
-
Deleting keys
-
Signing keys
-
Retrieving key stores
-
Setting and retrieving authentication policies
-
Setting use and management policies
See Unified Certificate Store Tutorial and Unified Keystore Tutorials for details of these tasks.
Copyright ©2010 Nokia Corporation and/or its subsidiary(-ies).
All rights
reserved. Unless otherwise stated, these materials are provided under the terms of the Eclipse Public License
v1.0.