Symmetric ciphers -- guide
What are symmetric ciphers?
Symmetric algorithms are much faster than asymmetric algorithms so are used to encrypt and decrypt large amounts of data. In an informal setting, symmetric ciphers can be thought of as a mapping of some plaintext to ciphertext, via some well-known transformation function, dependent on a single secret key. Symmetric algorithms have the property that if a message is encrypted under a given key, it can only be decrypted using the same key:
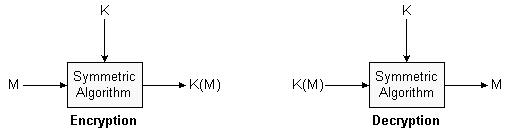
So it provides secrecy and also some kind of authentication. If Alice encrypts a secret using a key known only to her, then only she can access the secrets.
It can also be used for communication: if Alice shares a key with Bob (and only Bob), then she can encrypt her messages with that key and send it to Bob, and only Bob can decrypt them. In this case the key is a 'shared secret' enabling private communications.
There are two basic types of symmetric ciphers: block ciphers and stream ciphers.
Block and stream ciphers
Stream ciphers are essentially functions that are initialized with a key, and output a stream of pseudorandom bits, this 'keystream' is typically XOR-ed with the plaintext to generate the ciphertext. So they encrypt a bit of plaintext at a time. They map an n -bit stream of plaintext to a n -bit stream of ciphertext.
Block ciphers encrypt several bits at once in a fixed-size block. That is, they map m n -bit blocks of plaintext to m n -bit blocks of ciphertext. The cipher and its mode of operation define the block size: the plaintext is split up into appropriately-sized blocks and each block is fed into the cipher.
There are two issues here that don't occur with stream ciphers:
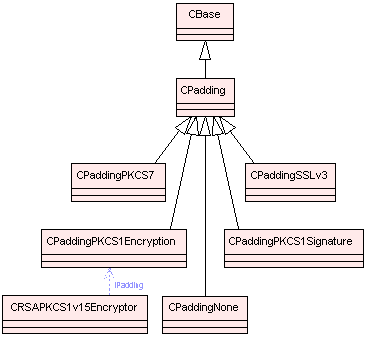
padding: the total size of the input has to be a multiple of the block size, so the plaintext usually has to be padded to fit (see the class CPadding). Optionally, instead of padding out a plaintext message to fit in a block, block ciphers allow buffering of partial input blocks until the remainder of the block is given as input. (see How does buffering work within the symmetric cipher framework? and PKCS#7).
combining blocks: if you just encrypt each plaintext block with the cipher and then concatenate the ciphertext blocks, then an attacker who knows something about the structure can switch the order of the ciphertext blocks to alter the meaning of the message. For example, if the plaintext includes instructions like 'pay £XXX to account holder ABC, reference number YYY', then an attacker could replace the encryption of XXX with some of the encryption of YYY. This leads to other techniques for combining blocks, called modes, where, for example, the output of the last block is fed into the input for the next one. So, the output is not just a function of that plaintext block and key, but is a function of that plaintext block, the key, and all preceding ciphertext blocks (see Symmetric Modes).
Both stream ciphers and block ciphers are provided by the API with a similar interface. Block ciphers usually need padding for non completed blocks. The API allows the user to choose the padding to be added at the end of the last encrypted block or to be checked and removed from the last decrypted block.
Types of symmetric algorithms supported
The following symmetric algorithms are supported:
Base classes and their derived classes
The symmetric cipher API is used by Networking (TLS/IPSec).
CSymmetricCipher is the abstract base class that allows a client to use the supported symmetric algorithms listed above. It allows clients to encrypt and decrypt without having to know anything about which encryption algorithm is currently in use.
The PKCS5 API (the TPKCS5KDF class, also see Password Based Encryption) offers Key Derivation Support that allows the derivation of deterministic arbitrary length byte streams from an input string. The output byte stream is generated using multiple iterations of a SHA-1 message digest (CSHA1) and is suitable for use as a cryptographic symmetric key.
The diagrams below show the main classes used in symmetric cipher framework. Blue dotted arrows indicate that a class is contained or used by another class. The arrows are labelled with the variable(s) through which the pointed class is accessible. The colour of the boxes indicates the type of Symbian class, i.e., M, C, R or T class. For detailed information on each component see the Cryptography API Reference material.
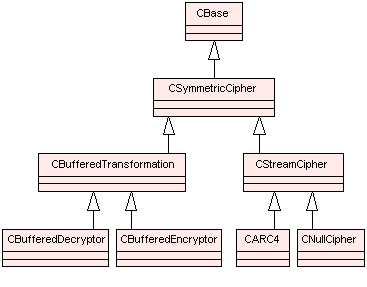
CSymmetricCipher and derived classes
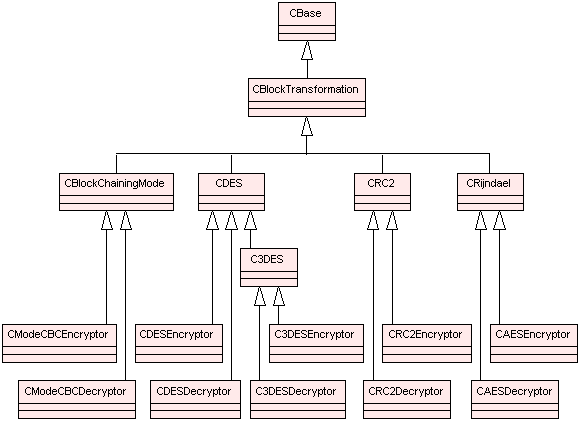
CBlockTransformation and derived classes
Copyright ©2010 Nokia Corporation and/or its subsidiary(-ies).
All rights
reserved. Unless otherwise stated, these materials are provided under the terms of the Eclipse Public License
v1.0.